Thank you for reading this post, don't forget to subscribe!
Why SBOM Matters: Beyond Penetration Testing and Source Code Review
In today’s software-driven world, the complexity of applications has grown exponentially. With this complexity comes an increased risk of vulnerabilities, especially when software components are sourced from third-party libraries, open-source repositories, or external vendors. To manage this risk effectively, organizations are turning to a powerful tool: the Software Bill of Materials (SBOM).
But what exactly is an SBOM, and how does it compare to established practices like penetration testing and source code review? More importantly, what stages do these methods operate in, and how much of your application’s security do they cover?
Let’s dive into the answers.
Understanding SBOM: A Digital Inventory of Software Components
An SBOM is a structured inventory of all components that make up a software product. It includes:
- Component names and versions
- Dependency relationships
- Licensing information
- Supplier details
- Known vulnerabilities (when integrated with vulnerability databases)
Think of it as the software equivalent of a nutrition label—providing transparency into what’s inside your application.
When Do SBOM, Penetration Testing, and Source Code Review Operate?
Each of these practices plays a distinct role at different stages of the software development lifecycle:
| Practice | Lifecycle Stage | Primary Focus |
|---|---|---|
| Penetration Testing | Pre-release & post-deployment | Runtime vulnerabilities, misconfigurations, exploitability |
| Source Code Review | Development | Code quality, logic flaws, insecure coding practices |
| SBOM | Build & Post-Deployment | Component inventory, dependency tracking, license compliance, vulnerability mapping |
This layered approach ensures that security is addressed from multiple angles—during development, at build time, and in production.
Each method contributes uniquely to the security posture of an application:
- Penetration Testing simulates real-world attacks to validate the effectiveness of security controls. If you’d like to see how this works in practice, explore our penetration testing services that help identify runtime vulnerabilities before they impact your production environment.
- Source Code Review is proactive, catching issues early in the development phase. Check out our Source Code Review services to secure your code before release.
- SBOM provides visibility into what’s inside the software, especially third-party components, and continues to be relevant post-deployment.
Security Coverage: How Much Does Each Method Cover?
While exact percentages can differ in scope, depth and quality. Based on industry insights and expert consensus, here’s an approximate breakdown of their coverage in terms of application security.
| Practice | Estimated Coverage | Strengths | Limitations |
|---|---|---|---|
| Penetration Testing | ~20–30% | Validates real-world exploitability and runtime issues | Snapshot in time; may miss dormant or hidden vulnerabilities |
| Source Code Review | ~30–40% | Identifies logic errors, insecure patterns, and coding flaws | Limited visibility into compiled binaries and third-party components |
| SBOM | ~40–50% | Tracks third-party dependencies, licenses, and known vulnerabilities | Doesn’t analyze runtime behavior or logic flaws |
Note: These percentages are not additive but complementary. Together, they form a robust, multi-layered security strategy
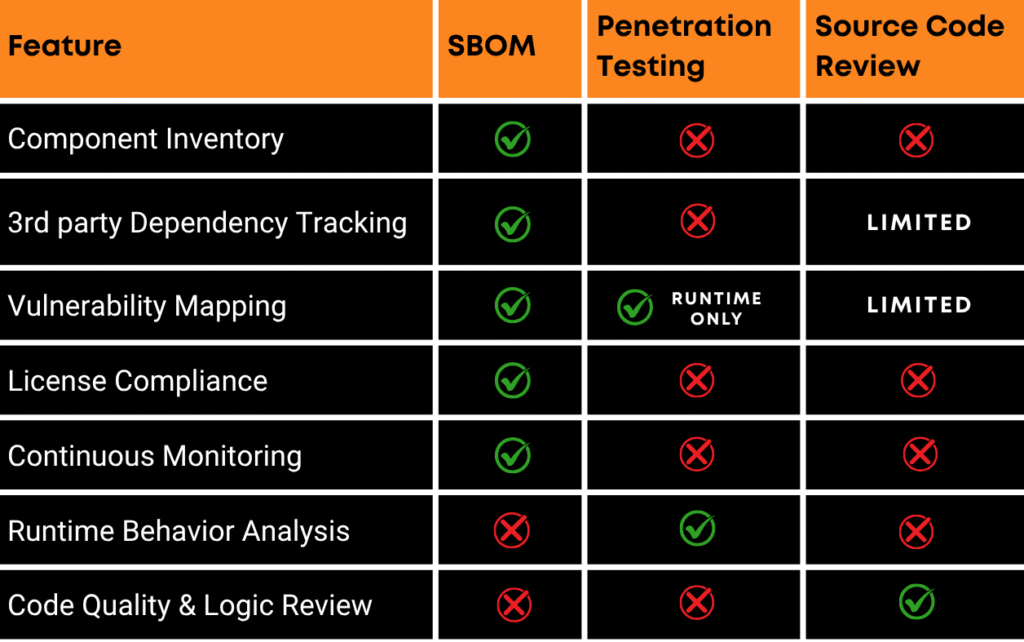
SBOM vs. Traditional Security Practices: A Complementary Approach
Refer the table below, SBOMs don’t replace penetration testing or code reviews—they complement them by filling critical visibility gaps.
How SBOMApp Can Help
While this blog focuses on the general importance of SBOMs, tools like SBOMApp are designed to simplify and automate SBOM generation, integration, and analysis. Whether you’re a developer, security analyst, or compliance officer, SBOMApp helps you maintain visibility, traceability, and security across your software assets.
Conclusion
SBOMs are not a replacement for penetration testing or source code reviews—they are a critical addition to your security toolkit. By providing deep visibility into your software’s composition, SBOMs empower organizations to manage risk, ensure compliance, and build trust in their software products.
As the software landscape continues to evolve, embracing SBOMs is not just smart—it’s essential.
Learn more in our detailed guide on the critical importance of SBOM compliance
Have Questions? We’re Here to Help
Just drop your details. Our experts will connect with you to guide your next steps — fast and simple


Comments are closed.